Homelab’s logical network was a lot more work than I thought to put together, but it has been a great exercise to finally put this down on paper.
In part one, I am trying to give some background to the services I run, and how I setup my network. I will have a follow-up with some more hardware based details, and more specific vm/containers.
To start, I have some EOL Nokia network gear for my core routing and use pfSense for edge firewall/VPN/HA. I have logically broken up these services in IP VRFs (Virtual Routing and Forwarding) or a Nokia specific service – a VPRN (Virtual Private Routed Network)
This allows me to control access between the VPRN services, through a firewall (pfSense) instead of relying on ACLs on the Nokia router, or moving all my routing to pfSense, which would slow performance. This, in my opinion, is the best of both worlds. Routers route, and firewalls inspect. Now when I have services on multiple networks, within the same VPRN, I get the benefit of wireline bandwidth as it will route like a normal router. Otherwise, if traffic needs to cross VPRNs, it will need to go through pfSense where firewall rules are evaluated.
Without further ado here is the drawing!
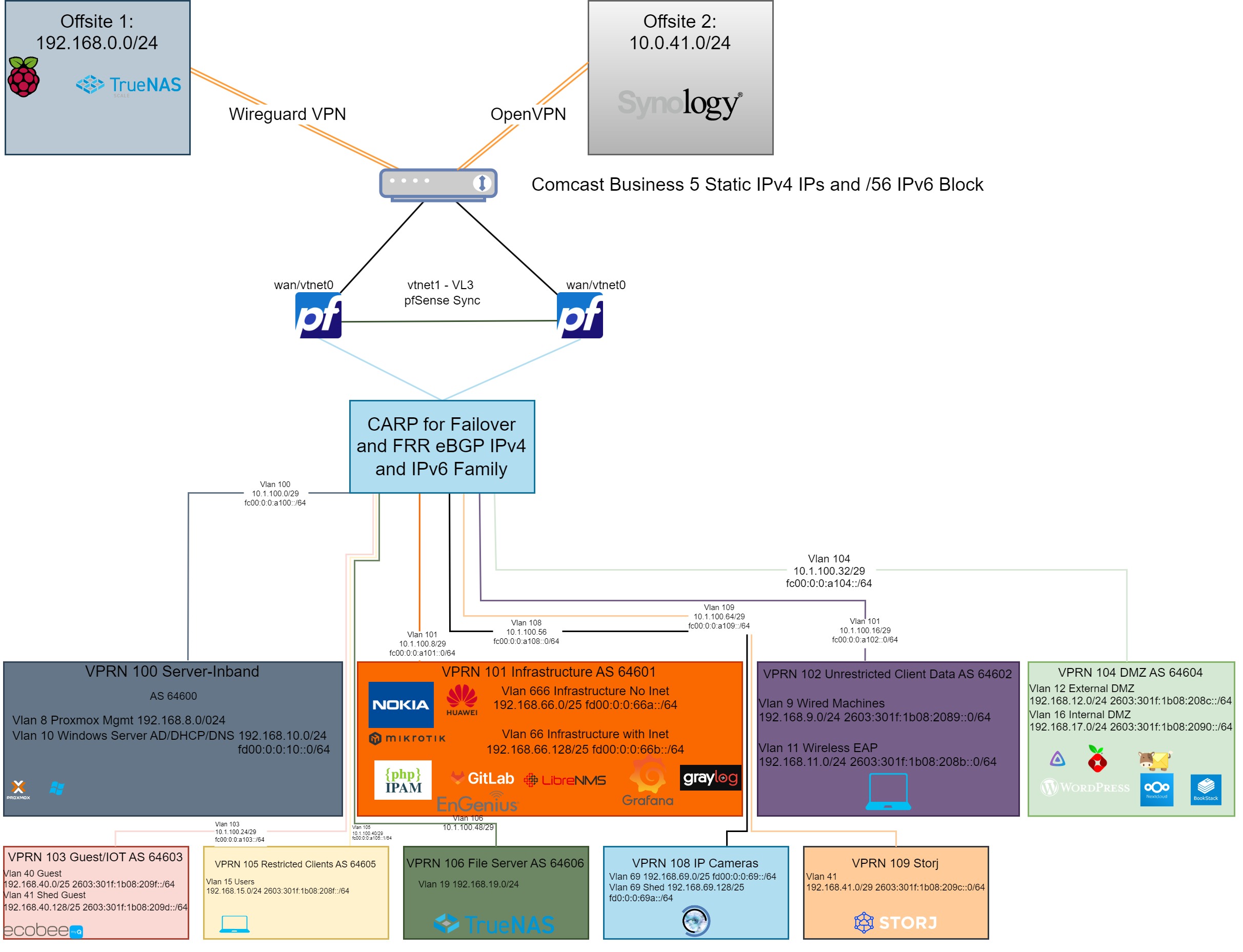
Here is a quick run down of the services from top down:
- Offsite:
- I run Truenas scale on an old server over a Wireguard site-to-site VPN running on a Raspberry Pi. This is not powered on all the time, and I use it to replicate snapshots from my main Truenas core’s SMB shares.
- The other offsite location I have is a Synology NAS, to which I also replicate Truenas core’s SMB shares using rsync.
- I have Comcast business service and several static IPv4 IPs and IPv6 block.
- On my Edge, I have two pfSense VMs running on two hypervisors which provide HA failover for themselves and my internal network.
- Below is a list of the VPRN services:
| VPRN | VPRN Name | Purpose | Notes |
| 100 | Inband/AD | Hypervisor gui mgmt, and AD Services | Critical AD services (DNS/DHCP/NPS) |
| 101 | Infrastructure services | Network hardware mgmt, and VMs running critical software | Syslog/snmp monitoring/stats |
| 102 | Unrestricted clients | Clients that have no rules blocking to other zones | TLS/PEAP WLAN clients or domain joined machines |
| 103 | Guest/IOT | Guest SSID and IOT devices | |
| 104 | DMZ | Mix of internal DMZ and inbound services allowed | Web/mail/NTP pool members |
| 105 | Restricted Devices | Devices that have access blocked to AD/infrastructure services | clients that do not need full access to the internal network |
| 106 | File Services | Mostly for SMB access | Truenas scale SMB shares |
| 108 | Cameras | NVR and cameras | Blueiris NVR and IP cameras |
| 109 | Storj | Storj node operator VM |
Hopefully that layout makes sense so you can understand how I went about separating these. Feel free to ask me questions! Now, let’s spend a little bit of time on the routing and how it looks:


I am using VPRN service 100 as an example. I send the default route via the eBGP neighbor (pfSense). Then if I look for another prefix that would be in another VPRN (this case 102) it does not route directly to that network; instead it goes to the firewall first even though both of these exist on the same router. A cleanup I want to do is to only send the default route from pfSense to these VPRNs, not on specific routes, but that will be a future blog post!
We can view the local configured subnets in the VPRN. These would be exported to pfSense so other VPRNs, and pfSense would know how to reach these hosts.

Finally, in pfSense, here is a quick shot of how the route table looks. First there is 192.168.8.0/25 that is in VPRN 100, and the 192.168.9.0/24 prefix that is in VPRN 102. Notice how they have two different eBGP next hop IPs which correspond to the interface on the Nokia router.

Part 2 I’ll dive into the FRR package in pfSense and the BGP setup on the Nokia router.